Cybersecurity researchers have discovered a new version of a well-known Android malware family dubbed FakeCall that employs voice phishing (aka vishing) techniques to trick users into parting with their personal information.
“FakeCall is an extremely sophisticated Vishing attack that leverages malware to take almost complete control of the mobile device, including the interception of incoming and outgoing calls,” Zimperium researcher Fernando Ortega said in a report published last week.
“Victims are tricked into calling fraudulent phone numbers controlled by the attacker and mimicking the normal user experience on the device.”
FakeCall, also tracked under the names FakeCalls and Letscall, has been the subject of multiple analyses by Kaspersky, Check Point, and ThreatFabric since its emergence in April 2022. Previous attack waves have primarily targeted mobile users in South Korea.

The names of the malicious package names, i.e., dropper apps, bearing the malware are listed below –
- com.qaz123789.serviceone
- com.sbbqcfnvd.skgkkvba
- com.securegroup.assistant
- com.seplatmsm.skfplzbh
- eugmx.xjrhry.eroreqxo
- gqcvctl.msthh.swxgkyv
- ouyudz.wqrecg.blxal
- plnfexcq.fehlwuggm.kyxvb
- xkeqoi.iochvm.vmyab
Like other Android banking malware families that are known to abuse accessibility services APIs to seize control of the devices and perform malicious actions, FakeCall uses it to capture information displayed on the screen and grant itself additional permissions as required.
Some of the other espionage features include capturing a wide range of information, such as SMS messages, contact lists, locations, and installed apps, taking pictures, recording a live stream from both the rear- and front-facing cameras, adding and deleting contacts, grabbing audio snippets, uploading images, and imitating a video stream of all the actions on the device using the MediaProjection API.
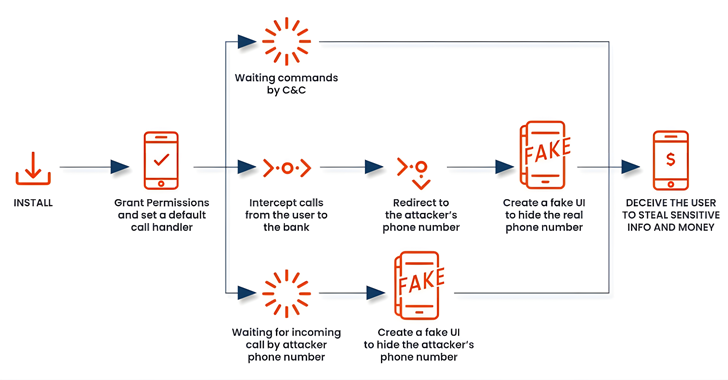
The newer versions are also designed to monitor Bluetooth status and the device screen state. But what makes the malware more dangerous is that it instructs the user to set the app as the default dialer, thus giving it the ability to keep tabs on all incoming and outgoing calls.
This not only allows FakeCall to intercept and hijack calls, but also enables it to modify a dialed number, such as those to a bank, to a rogue number under their control, and lure the victims into performing unintended actions.
In contrast, previous variants of FakeCall were found to prompt users to call the bank from within the malicious app imitating various financial institutions under the guise of a loan offer with a lower interest rate.

“When the compromised individual attempts to contact their financial institution, the malware redirects the call to a fraudulent number controlled by the attacker,” Ortega said.
“The malicious app will deceive the user, displaying a convincing fake UI that appears to be the legitimate Android’s call interface showing the real bank’s phone number. The victim will be unaware of the manipulation, as the malware’s fake UI will mimic the actual banking experience, allowing the attacker to extract sensitive information or gain unauthorized access to the victim’s financial accounts.”
The emergence of novel, sophisticated mishing (aka mobile phishing) strategies highlights a counter-response to improved security defenses and the prevalent use of caller identification applications, which can flag suspicious numbers and warn users of potential spam.
In recent months, Google has also been experimenting with a security initiative that automatically blocks the sideloading of potentially unsafe Android apps, counting those that request accessibility services, across Singapore, Thailand, Brazil, and India.