A new information-stealing malware has set its sights on Apple’s macOS operating system to siphon sensitive information from compromised devices.
Dubbed MacStealer, it’s the latest example of a threat that uses Telegram as a command-and-control (C2) platform to exfiltrate data. It primarily affects devices running macOS versions Catalina and later running on M1 and M2 CPUs.
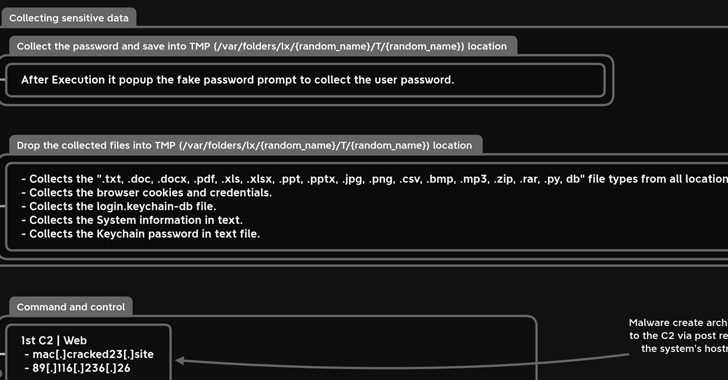
“MacStealer has the ability to steal documents, cookies from the victim’s browser, and login information,” Uptycs researchers Shilpesh Trivedi and Pratik Jeware said in a new report.
First advertised on online hacking forums at the start of the month, it is still a work in progress, with the malware authors planning to add features to capture data from Apple’s Safari browser and the Notes app.
In its current form, MacStealer is designed to extract iCloud Keychain data, passwords and credit card information from browsers like Google Chrome, Mozilla Firefox, and Brave. It also features support for harvesting Microsoft Office files, images, archives, and Python scripts.
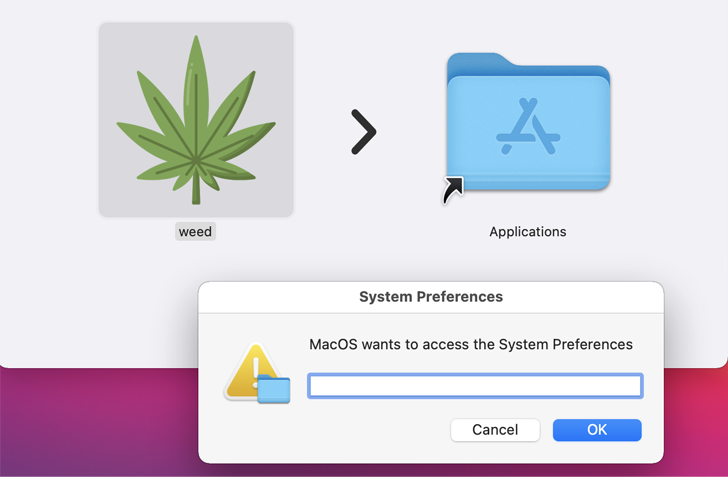
The exact method used to deliver the malware is not known, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a fake password prompt to harvest the passwords under the guise of seeking access to the System Settings app.
MacStealer is one of several info-stealers that have surfaced just over the past few months and adds to an already large number of similar tools currently in the wild.
This also includes another piece of new C#-based malware called HookSpoofer that’s inspired by StormKitty and comes with keylogging and clipper abilities and transmits the stolen data to a Telegram bot.
Another browser cookie-stealing malware of note is Ducktail, which also uses a Telegram bot to exfiltrate data and re-emerged in mid-February 2023 with improved tactics to sidestep detection.
This involves “changing the initial infection from an archive containing a malicious executable to an archive containing a malicious LNK file that would start the infection chain,” Deep Instinct researcher Simon Kenin said earlier this month.
Discover the Hidden Dangers of Third-Party SaaS Apps
Are you aware of the risks associated with third-party app access to your company’s SaaS apps? Join our webinar to learn about the types of permissions being granted and how to minimize risk.
RESERVE YOUR SEAT
Stealer malware is typically spread through different channels, including email attachments, bogus software downloads, and other social engineering techniques.
To mitigate such threats, it’s recommended that users keep their operating system and security software up to date and avoid downloading files or clicking links from unknown sources.
“As Macs have become increasingly popular in the enterprise among leadership and development teams, the more important the data stored on them is to attackers,” SentinelOne researcher Phil Stokes said last week.