Cybersecurity researchers are warning that a command-and-control (C&C) framework called Winos is being distributed within gaming-related applications like installation tools, speed boosters, and optimization utilities.
“Winos 4.0 is an advanced malicious framework that offers comprehensive functionality, a stable architecture, and efficient control over numerous online endpoints to execute further actions,” Fortinet FortiGuard Labs said in a report shared with The Hacker News. “Rebuilt from Gh0st RAT, it includes several modular components, each handling distinct functions.”
Campaigns distributing Winos 4.0 were documented back in June by Trend Micro and the KnownSec 404 Team. The cybersecurity companies are tracking the activity cluster under the names Void Arachne and Silver Fox.

Attacks have been observed targeting Chinese-speaking users, leveraging black hat Search Engine Optimization (SEO) tactics, social media, and messaging platforms like Telegram to distribute the malware.
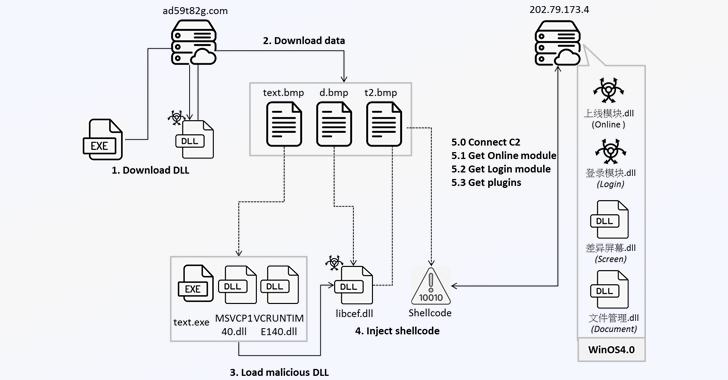
Fortinet’s latest analysis shows that users who end up running the malicious game-related applications trigger a multi-stage infection process that begins with retrieving a fake BMP file from a remote server (“ad59t82g[.]com”) that’s then decoded into a dynamic-link library (DLL).
The DLL file takes care setting up the execution environment by downloading three files from the same server: t3d.tmp, t4d.tmp, and t5d.tmp, the first two of which are subsequently unpacked to obtain the next set of payloads comprising an executable (“u72kOdQ.exe”) and three DLL files, including “libcef.dll.”

“The DLL is named ‘学籍系统,’ meaning ‘Student Registration System,’ suggesting that the threat actor may be targeting educational organizations,” Fortinet said.
In the next step, the binary is employed to load “libcef.dll,” which then extracts and executes the second-stage shellcode from t5d.tmp. The malware proceeds to establish contact with its command-and-control (C2) server (“202.79.173[.]4” using the TCP protocol and retrieve another DLL (“上线模块.dll”).
The third-stage DLL, part of Winos 4.0, downloads encoded data from the C2 server, a fresh DLL module (“登录模块.dll”) that’s responsible for harvesting system information, copying clipboard content, gathering data from cryptocurrency wallet extensions like OKX Wallet and MetaMask, and facilitating backdoor functionality by awaiting further commands from the server.

Winos 4.0 also enables the delivery of additional plugins from the C2 server that allow it to capture screenshots and upload sensitive documents from the compromised system.
“Winos4.0 is a powerful framework, similar to Cobalt Strike and Sliver, that can support multiple functions and easily control compromised systems,” Fortinet said. “Threat campaigns leverage game-related applications to lure a victim to download and execute the malware without caution and successfully deploy deep control of the system.”