The threat actor known as Patchwork has been linked to a cyber attack targeting entities with ties to Bhutan to deliver the Brute Ratel C4 framework and an updated version of a backdoor called PGoShell.
The development marks the first time the adversary has been observed using the red teaming software, the Knownsec 404 Team said in an analysis published last week.
The activity cluster, also called APT-C-09, Dropping Elephant, Operation Hangover, Viceroy Tiger, and Zinc Emerson, is a state-sponsored actor likely of Indian origin.

Known for conducting spear-phishing and watering hole attacks against China and Pakistan, the hacking crew is believed to be active since at least 2009, according to data shared by Chinese cybersecurity firm QiAnXin.
Last July, Knownsec 404 disclosed details of an espionage campaign aimed at universities and research organizations in China that leveraged a .NET-based implant codenamed EyeShell to fetch and execute commands from an attacker-controlled server, run additional payloads, and capture screenshots.
Then earlier this February, it was found that the threat actor had employed romance-themed lures to ensnare victims in Pakistan and India and compromise their Android devices with a remote access trojan dubbed VajraSpy.
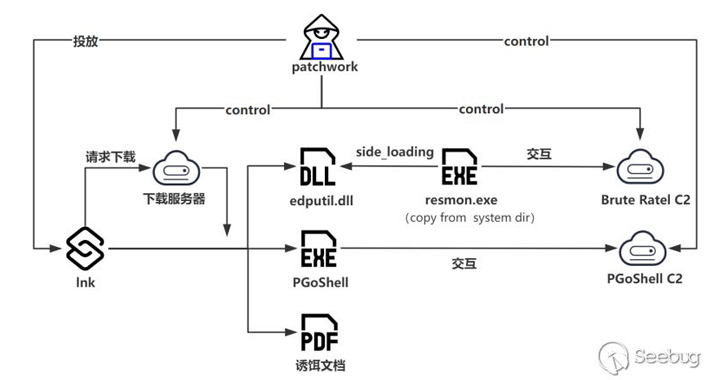
The starting point of the latest observed attack chain is a Windows shortcut (LNK) file that’s designed to download a decoy PDF document from a remote domain impersonating the UNFCCC-backed Adaptation Fund, while stealthily deploying Brute Ratel C4 and PGoShell retrieved from a different domain (“beijingtv[.]org”).
“PGoShell is developed in the Go programming language; overall, it offers a rich set of functionalities, including remote shell capabilities, screen capture, and downloading and executing payloads,” the cybersecurity company said.
The development comes months after APT-K-47 – another threat actor sharing tactical overlaps with SideWinder, Patchwork, Confucius, and Bitter – was attributed to attacks involving the use of ORPCBackdoor as well as previously undocumented malware like WalkerShell, DemoTrySpy, and NixBackdoor to harvest data and execute shellcode.
The attacks are also notable for deploying an open-source command-and-control (C2) framework known as Nimbo-C2, which “enables a wide range of remote control functionalities,” Knownsec 404 said.