The pay-per-install (PPI) malware downloader service known as PrivateLoader is being used to distribute a previously documented information-stealing malware dubbed RisePro.
Flashpoint spotted the newly identified stealer on December 13, 2022, after it discovered “several sets of logs” exfiltrated using the malware on an illicit cybercrime marketplace called Russian Market.
A C++-based malware, RisePro is said to share similarities with another info-stealing malware referred to as Vidar stealer, itself a fork of a stealer codenamed Arkei that emerged in 2018.

“The appearance of the stealer as a payload for a pay-per-install service may indicate a threat actor’s confidence in the stealer’s abilities,” the threat intelligence company noted in a write-up last week.
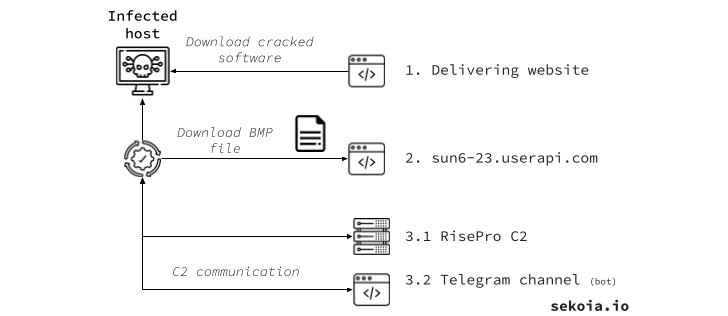
Cybersecurity firm SEKOIA, which released its own analysis of RisePro, further identified partial source code overlaps with PrivateLoader. This encompasses the string scrambling mechanism, HTTP method and port setup, and the HTTP message obfuscation method.
PrivateLoader, as the name indicates, is a download service that enables its subscribers to deliver malicious payloads to target hosts.
It has been used in the past to deliver Vidar Stealer, RedLine Stealer, Amadey, DanaBot, and NetDooka, among others, while masquerading as pirated software hosted on decoy sites or compromised WordPress portals that appear prominently on search results.
RisePro is no different from other stealers in that it’s capable of stealing a wide range of data from as many as 36 web browsers, including cookies, passwords, credit cards, crypto wallets, as well as gathering files of interest and loading more payloads.
It’s offered for sale on Telegram, with the malware’s developer also making available a Telegram channel that enables criminal actors to interact with infected systems by providing a bot ID created by the stealer and sent to a remote server post a successful breach.
Also part of the malware’s infrastructure is an administration panel hosted at a domain named my-rise[.]cc that allows access to stolen data logs, but only after signing into an account with a valid set of credentials.
It’s currently not clear if RisePro is authored by the same set of threat actors behind PrivateLoader, and if it’s exclusively bundled alongside the PPI service.
“PrivateLoader is still active and comes with a set of new capabilities,” SEKOIA said. “Similarities between the stealer and PrivateLoader cannot be ignored and provides additional insight into the threat actor expansion.”