Cybersecurity researchers have uncovered a new malicious campaign that leverages a technique called Bring Your Own Vulnerable Driver (BYOVD) to disarm security protections and ultimately gain access to the infected system.
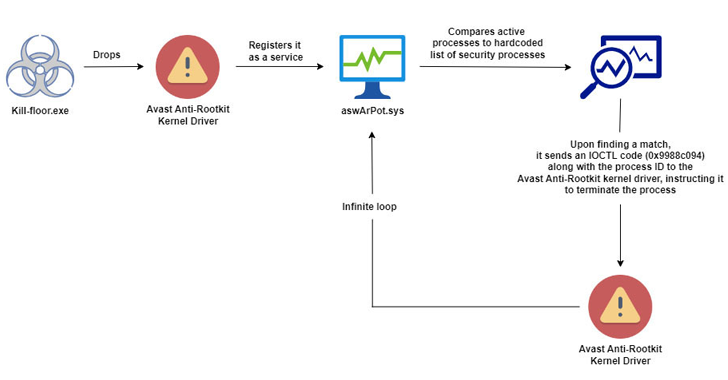
“This malware takes a more sinister route: it drops a legitimate Avast Anti-Rootkit driver (aswArPot.sys) and manipulates it to carry out its destructive agenda,” Trellix security researcher Trishaan Kalra said in an analysis published last week.
“The malware exploits the deep access provided by the driver to terminate security processes, disable protective software, and seize control of the infected system.”
The starting point of the attack is an executable file (kill-floor.exe) that drops the legitimate Avast Anti-Rootkit driver, which is subsequently registered as a service using Service Control (sc.exe) to perform its malicious actions.

Once the driver is up and running, the malware gains kernel-level access to the system, allowing it to terminate a total of 142 processes, including those related to security software, that could otherwise raise an alarm.
This is accomplished by taking snapshots of the actively running processes on the system and checking their names against the hard-coded list of processes to kill.

“Since kernel-mode drivers can override user-mode processes, the Avast driver is able to terminate processes at the kernel level, effortlessly bypassing the tamper protection mechanisms of most antivirus and EDR solutions,” Kalra said.
The exact initial access vector used to drop the malware is currently not clear. It’s also not known how widespread these attacks are and who are the targets.
That said, BYOVD attacks have become an increasingly common method adopted by threat actors to deploy ransomware in recent years, as they reuse signed but flawed drivers to bypass security controls.
Earlier this May, Elastic Security Labs revealed details of a GHOSTENGINE malware campaign that took advantage of the Avast driver to turn off security processes.