Threat actors associated with the Roaming Mantis attack campaign have been observed delivering an updated variant of their patent mobile malware known as Wroba to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking.
Kaspersky, which carried out an analysis of the malicious artifact, said the feature is designed to target specific Wi-Fi routers located in South Korea.
Roaming Mantis, also known as Shaoye, is a long-running financially motivated operation that targets Android smartphone users with malware capable of stealing bank account credentials as well as harvesting other kinds of sensitive information.
Although primarily targeting the Asian region since 2018, the hacking crew was detected expanding its victim range to include France and Germany for the first time in early 2022 by camouflaging the malware as the Google Chrome web browser application.
The attacks leverage smishing messages as the initial intrusion vector of choice to deliver a booby-trapped URL that either offers a malicious APK or redirects the victim to phishing pages based on the operating system installed in the mobile devices.
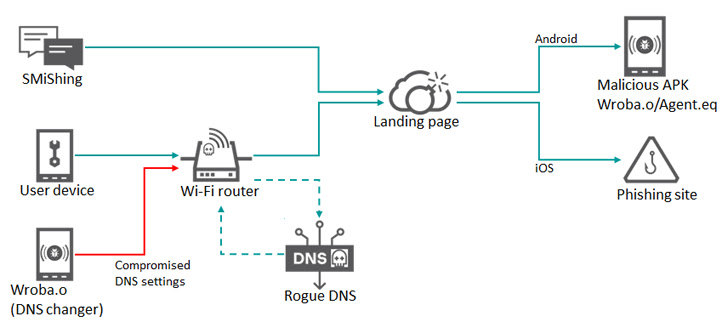
Alternatively, some compromises have also leveraged Wi-Fi routers as a means to take unsuspecting users to a fake landing page by using a technique called DNS hijacking, in which DNS queries are manipulated in order to redirect targets to bogus sites.
Regardless of the method used, the intrusions pave the way for the deployment of a malware dubbed Wroba (aka MoqHao and XLoader) that’s capable of carrying out a slew of nefarious activities.
The latest update to Wroba, per the Russian cybersecurity company, involves a DNS changer function that’s engineered to detect certain routers based on their model numbers and poison their DNS settings.
“The new DNS changer functionality can manage all device communications using the compromised Wi-Fi router, such as redirecting to malicious hosts and disabling updates of security products,” Kaspersky researcher Suguru Ishimaru said.
The underlying idea is to cause devices connected to the breached Wi-Fi router to be redirected to web pages controlled by the threat actor for further exploitation. Given that some of these pages deliver the Wroba malware, the attack chain effectively creates a steady stream of “bots” that can be weaponized to break into healthy Wi-Fi routers.
It’s notable that the DNS changer program is exclusively used in South Korea. However, the Wroba malware in itself has been spotted targeting victims in Austria, France, Germany, India, Japan, Malaysia, Taiwan, Turkey, and the U.S. via smishing.
“Users with infected Android devices that connect to free or public Wi-Fi networks may spread the malware to other devices on the network if the Wi-Fi network they are connected to is vulnerable,” the researcher said.
