The Russia-linked Gamaredon group attempted to unsuccessfully break into a large petroleum refining company within a NATO member state earlier this year amid the ongoing Russo-Ukrainian war.
The attack, which took place on August 30, 2022, is just one of multiple attacks orchestrated by the advanced persistent threat (APT) that’s attributed to Russia’s Federal Security Service (FSB).
Gamaredon, also known by the monikers Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder, has a history of primarily going after Ukrainian entities and, to a lesser extent, NATO allies to harvest sensitive data.
“As the conflict has continued on the ground and in cyberspace, Trident Ursa has been operating as a dedicated access creator and intelligence gatherer,” Palo Alto Networks Unit 42 said in a report shared with The Hacker News. “Trident Ursa remains one of the most pervasive, intrusive, continuously active and focused APTs targeting Ukraine.”

Unit 42’s continued monitoring of the group’s activities has uncovered more than 500 new domains, 200 malware samples, and multiple shifts in its tactics over the past 10 months in response to ever-changing and expanding priorities.
Beyond cyberattacks, the larger security community is said to have been at the receiving end of threatening tweets from a purported Gamaredon associate, highlighting the intimidation techniques adopted by the adversary.
Other noteworthy methods include the use of Telegram pages to look up command-and-control (C2) servers and fast flux DNS to rotate through many IP addresses in a short span of time to make IP-based denylisting and takedown efforts harder.
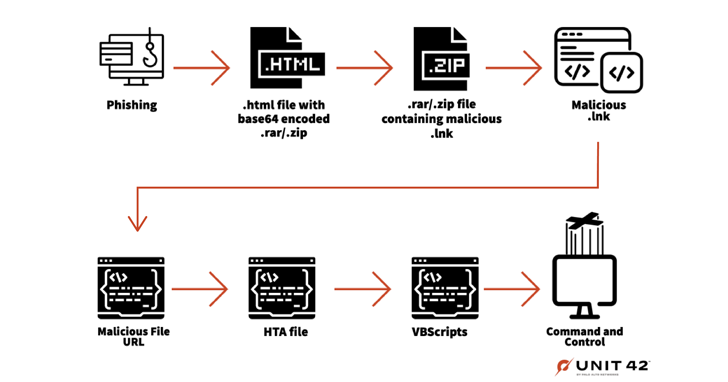
The attacks themselves entail the delivery of weaponized attachments embedded within spear-phishing emails to deploy a VBScript backdoor on the compromised host that’s capable of establishing persistence and executing additional VBScript code supplied by the C2 server.
Gamaredon infection chains have also been observed leveraging geoblocking to limit the attacks to specific locations along with utilizing dropper executables to launch next-stage VBScript payloads, which subsequently connect to the C2 server to execute further commands.
The geoblocking mechanism functions as a security blindspot as it reduces the visibility of the threat actor’s attacks outside of the targeted countries and makes its activities more difficult to track.
“Trident Ursa remains an agile and adaptive APT that does not use overly sophisticated or complex techniques in its operations,” the researchers said. “In most cases, they rely on publicly available tools and scripts – along with a significant amount of obfuscation – as well as routine phishing attempts to successfully execute their operations.”
