Operational technology (OT) cybersecurity is a challenging but critical aspect of protecting organizations’ essential systems and resources. Cybercriminals no longer break into systems, but instead log in – making access security more complex and also more important to manage and control than ever before. In an effort to solve the access-related challenges facing OT and critical infrastructure operators, the team at Cyolo built a zero-trust access platform designed to meet the unique safety, security, and uptime requirements of OT and industrial control systems (ICS) environments.
Let’s look under the hood:
The Cyolo solution is a high-powered combination of Zero Trust Network Access (ZTNA), Identity Provider (IdP), and Privileged Access Management (PAM). What makes this approach stand out from the pack is that other ZTNA solutions do not offer IdP or PAM capabilities, while Identity and Access Management tools (IdPs and PAMs) do not extend connectivity. And unlike other players in the secure remote access space, Cyolo does not require a cloud connection or the installation of an endpoint agent. This enables the platform to tackle some difficult connectivity use cases that many organizations struggle with.
How the Cyolo Platform Works
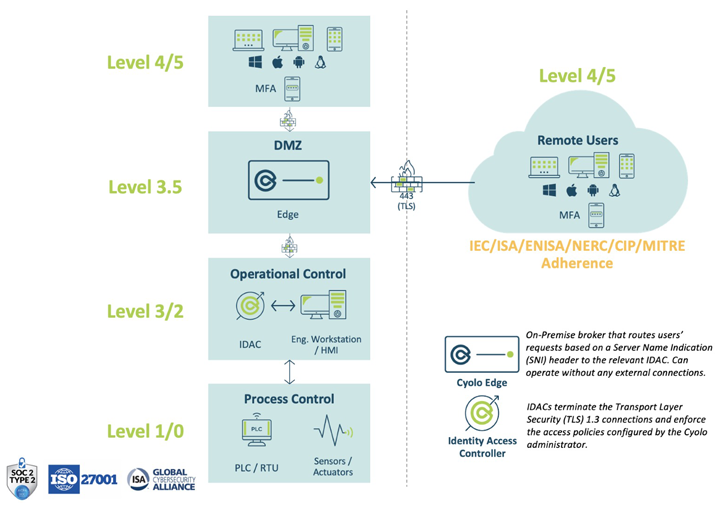 |
| Figure 1: Architectural layout of a Cyolo deployment |
The core building blocks of the Cyolo platform are Identity Access Controllers (IDACs) and Edges.
- Identity Access Controller (IDAC): IDACs terminate the Transport Layer Security (TLS) 1.3 connections and enforce the access policies configured by the Cyolo administrator. As a ‘reverse-proxy,’ all decryption and enforcement occur behind organizational firewalls.
- Edge Brokers: Edges are on-premises brokers that route users’ requests based on a Server Name Indication (SNI) header to the relevant IDAC. In all deployment models, the Edge routes traffic from the users to the IDACs. Notably, Edges can operate without any external connections and never decrypt any traffic, making Cyolo a rare zero-trust access solution that actually adheres to the principles of zero trust.
Cyolo can be deployed on-premises, in a SaaS model or, most commonly, in a hybrid version of the two. The on-premises components can be fully isolated and non-IP connected for additional security, as needed. These are the core elements needed for each deployment method:
- IdP Connection: Identity providers (IdPs) ensure the user seeking access is who or what they claim to be across multiple platforms, applications, and networks. Cyolo can integrate with your existing IdP, or you can use Cyolo’s local IdP that is included as part of the IDAC setup. The IDAC connects directly to the IdP (not through the Edges).
- IDAC Outbound Communication: IDACs always communicate outbound, whether they connect users’ sessions coming from the Edges (on port 443) or whether they communicate with the published applications they serve (on their specific port).
Product Deep Dive and Differentiation
Now, let’s take a deeper look into the Cyolo platform and see what distinguishes it from current approaches to access security and other tools on the market.
At first glance, the platform has a clean and easy to navigate user interface. It is set up to manage and administer the access of users to specific applications, and it brokers this access via a set of zero-trust policies. Looking a bit further, it logs many details about all user activity and has a robust application programming interface (API).
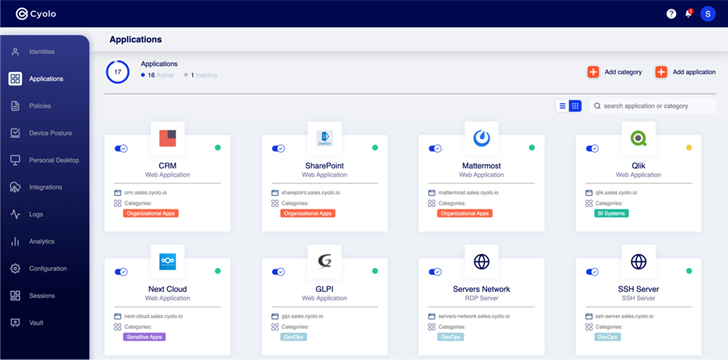 |
| Figure 2: Main page on the Cyolo administrator dashboard |
Identity: The Cyolo platform can act as a standalone identity source with users being added via file import, System for Cross-domain Identity Management (SCIM), or user self-enrollment. This is especially beneficial when onboarding third-party vendors and contractors who you may not want to add to your company’s IdP. Each user can be added to specific groups, which are used to grant access to specific applications or services, based on policies. The workflow to add users is easy and additional authentication steps, such as multi-factor authentication (MFA), can be added as a requirement.
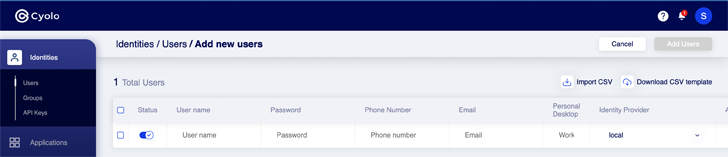 |
| Figure 3: Adding a new user in the Cyolo dashboard |
Cyolo can also work with all standard IdPs, such as Okta, Active Directory, Azure AD, Ping, etc. If companies have multiple IdPs, Cyolo can federate them and allow the most appropriate IdP for a particular access request to be used.
Applications: Cyolo provides connectivity to all applications based on valid identity, and then inserts credentials on behalf of the user to enable a full Single Sign-On (SSO) experience. This simplifies the log in process for users and helps eliminate the need for generic accounts or shared passwords, which can create added risk.
Cyolo can also extend secure access to legacy and custom-built applications to enable MFA and SSO for these challenging resources. This capability is most useful in the OT sector, which depends heavily on older equipment and systems that do communicate with Security Assertion Markup Language (SAML) or OpenID Connect (OIDC).
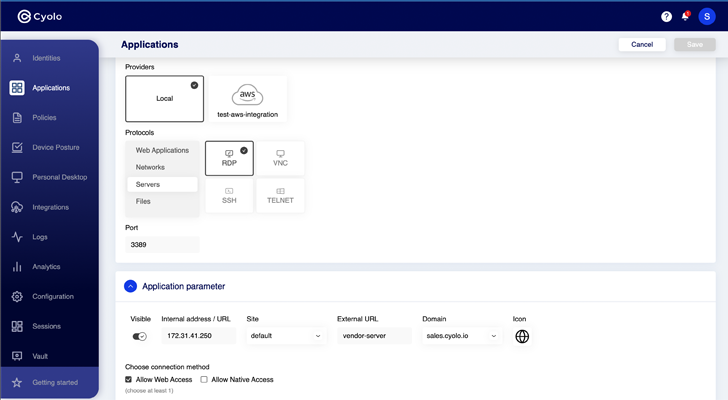 |
| Figure 4: Configuring applications in the Cyolo platform |
Policies: Each application is configured to require specific access parameters that account for individual users and groups, along with contextual details such as time of day or location. Two interesting features are the ability to require approval prior to access and the enforcement of recording for each access session.
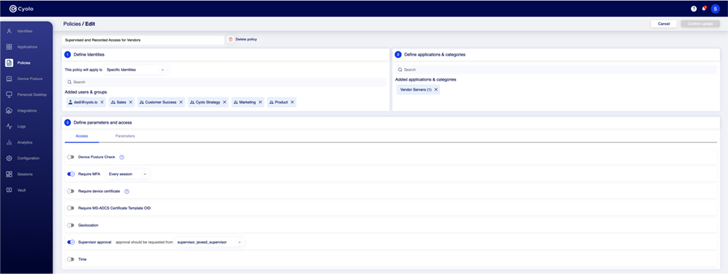 |
| Figure 5: Configuring policies between identities and applications in the Cyolo platform |
Logs: All activity on the platform is tracked in an easily exportable log. This is especially helpful when the Cyolo tool is providing SSO for an application that normally uses a generic username and password. Additionally, because Cyolo includes a password vault, it can securely store and rotate the shared password, with the log tracking exactly which user accessed the application or service.
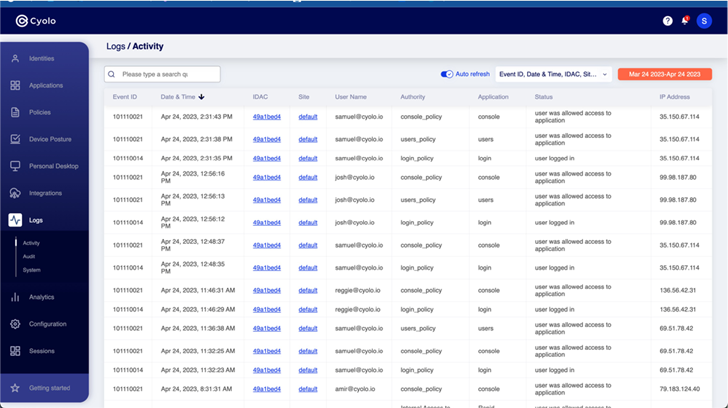 |
| Figure 6: Activity log within the Cyolo platform |
Additional Observations:
- Because Cyolo does not require a cloud connection to operate, the solution is ideal for companies who need to isolate critical segments of their network and restrict access to them. This is common for OT/ICS operators who want to tightly manage remote and third-party access into these areas.
- Remote access is sometimes hampered because the security tool requires an agent to be installed on an endpoint device. Cyolo does not require an agent to operate, making it easy to use for third parties, external contractors, or business partners.
- Their IDACs and Edge are containerized software applications (Docker containers), so they can be loaded onto a variety of form factors, such as virtual machines or hardened servers. This makes deployment simple and fast, as there is no need to interrupt traffic to install.
Conclusions
It’s clear that the Cyolo team recognizes the importance of a good, simple user experience. After all, any security or access tool must be easy for end users if it is to have any hope of achieving maximum adoption.
When an end user logs in to the Cyolo platform, they see only the tools, resources, and applications they need to perform their work. This is configured based on the polices for their identity and the specific application they are accessing and is enforced at the IDAC level within the organization’s trusted boundary. After the user selects the application they want to access, the Cyolo platform will manage all the connectivity and credential insertion for a fast and complete SSO experience. The beauty of this is that the user’s workflow is not impacted (in some set-ups, the user may not even know they’re using the Cyolo platform at all), yet the benefit to security posture is substantial.
 |
| Figure 7: Cyolo End-User Applications Portal |
One additional feature worth noting is the Cyolo platform’s management of Remote Desktop Protocol (RDP) connections into OT environments. With Cyolo’s ability to act as an IdP, adding an external (third-party) user was very easy. Layering additional security layers, like MFA, supervisor approval, and full audio/visual recording, were intuitive to set up and provide a valuable record of a user’s activity while connected. These capabilities demonstrate the power of integrating connectivity with IAM policies.
This short demo shows side-by-side user and admin screens to illustrate the workflow for a Native (or Web) RDP session with supervised access and recording.
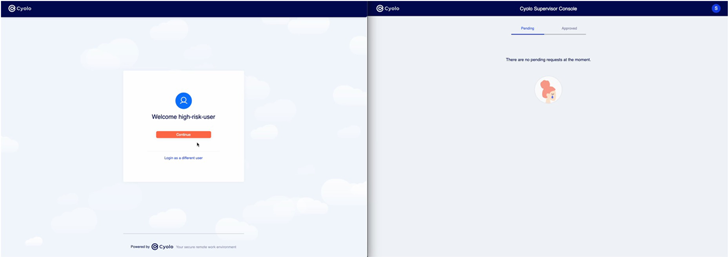 |
| Video 1: Quick demo of supervised access, without an agent, to a remote desktop via RDP |
Overall, the Cyolo platform is a versatile tool that can help solve some of the more difficult use cases plaguing many security operators today. By focusing on connectivity, identity validation, and access management, Cyolo brings a ton of horsepower to the table. And the best part is that they do not leave any application or service out and they specialize in tough scenarios, such as vendor access to OT environments. If you have a challenge that has been difficult to solve, it may be time to give Cyolo a closer look.
To learn more about Cyolo, click here.
