In the last decade, there has been a growing disconnect between front-line analysts and senior management in IT and Cybersecurity. Well-documented challenges facing modern analysts revolve around a high volume of alerts, false positives, poor visibility of technical environments, and analysts spending too much time on manual tasks.
The Impact of Alert Fatigue and False Positives
Analysts are overwhelmed with alerts. The knock-on effect of this is that fatigued analysts are at risk of missing key details in incidents, and often conduct time-consuming triaging tasks manually only to end up copying and pasting a generic closing comment into a false positive alert.
It is likely that there will always be false positives. And many would argue that a false positive is better than a false negative. But for proactive actions to be made, we must move closer to the heart of an incident. That requires diving into how analysts conduct the triage and investigation process.
SHQ Response Platform for Triage and Investigation
A typical triage process is often manual, and leverages analysts to perform individual log searches for contextual information. From this information, they begin to piece together a story of what has occurred and provide an idea of the overall risk scale.
The SHQ Response Platform utilizes Artificial Intelligence (AI) for log correlation, pulling information from different sources and visualizing it in a single incident page. From this, critical data is presented across a clear timeline, and artifacts are updated on the portal automatically.
By having the most important data presented in one place, an investigating analyst can cut through the noise and stay in one interface. They no longer need to pivot across multiple log sources or conduct manual SIEM searches to gather the relevant logs to then understand the story of a security incident.
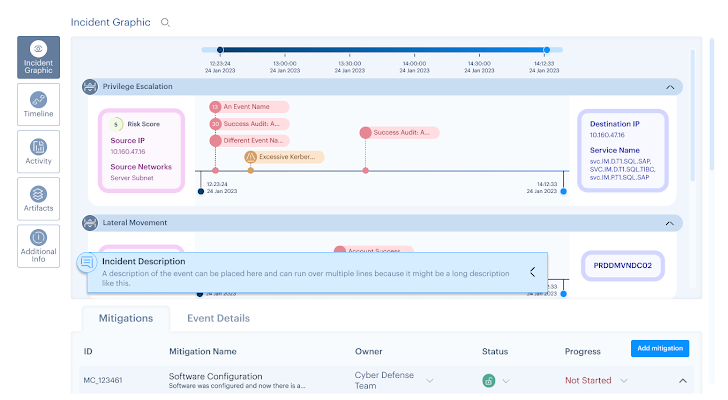 |
| Figure 1: Incident Graphic, SHQ Response Platform ©2024 SecurityHQ |
The timeline function also allows an analyst to investigate the logic behind an alert or use case trigger. This is shown with the relevant Indicators of Compromise (IoCs), which can be automatically blocked using back-end integrated tools.
Incident Response Platform for Senior Stakeholders
Overwhelmed analysts swamped by false positives is endemic. Head of Global SOC operations at SecurityHQ, Deodatta Wandhekar, put it best by explaining that:
‘Sixty percent of SOC Incidents are repeat findings that keep re-surfacing due to underlying unmitigated risks. The actors may be different; however, the risk is mostly the same. This is causing significant alert fatigue.’
One must consider how to bridge this gap, with both a clear focus on business objectives and risk appetite, while retaining a level of technical detail.
Risk Register for Collaboration & Strategy
SecurityHQ’s built-in Risk Register allows analysts and business leaders to work together to drive mitigation activities, using the technical acumen of operational staff to inform strategic business decisions.
This enables analysts to play a role in steering a cybersecurity program. By having a level of technical ownership, a more collaborative approach is fostered between operational analysts and management staff. It also allows once-overworked analysts to clearly see the fruits of their labor reflected in wider business practices.
Next Steps
SecurityHQ as both a consultative partner, and as the owner of such a platform, contributes to developing a better relationship between management and analysts by providing an intuitive, and executive-friendly, risk register.
From here, the focus on proactive approaches and roadmaps over simply ‘firefighting’ and closing incidents within a Service Level Agreement (SLA) creates the opportunity for meaningful change in a company.
For more information, speak to an expert here. If you suspect a security incident, report an incident here.
Note: This article was expertly written by Tim Chambers, Senior Cyber Security Manager at SecurityHQ
