Government organizations in Central Asia are the target of a sophisticated espionage campaign that leverages a previously undocumented strain of malware dubbed DownEx.
Bitdefender, in a report shared with The Hacker News, said the activity remains active, with evidence likely pointing to the involvement of Russia-based threat actors.
The Romanian cybersecurity firm said it first detected the malware in a highly targeted attack aimed at foreign government institutions in Kazakhstan in late 2022. Subsequently, another attack was observed in Afghanistan.
The use of a diplomat-themed lure document and the campaign’s focus on data exfiltration suggests the involvement of a state-sponsored group, although the exact identity of the hacking outfit remains indeterminate at this stage.

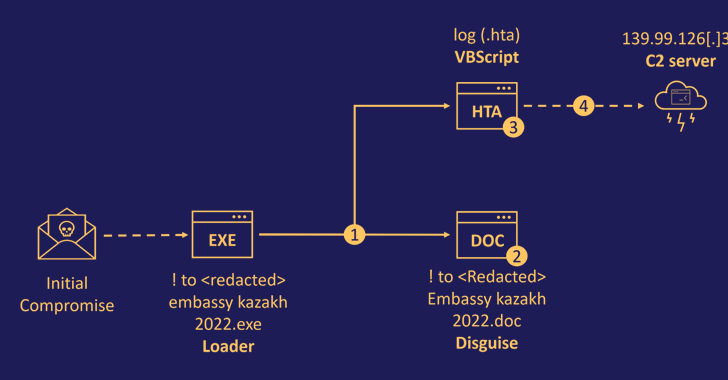
The initial intrusion vector for the campaign is suspected to be a spear-phishing email bearing a booby-trapped payload, which is a loader executable that masquerades as a Microsoft Word file.
Opening the attachment leads to the extraction of two files, including a decoy document that’s displayed to the victim while a malicious HTML application (.HTA) with embedded VBScript code runs in the background.
The HTA file, for its part, is designed to establish contact with a remote command-and-control (C2) server to retrieve a next-stage payload. While the exact nature of the malware is not unknown, it’s said to be a backdoor to establish persistence.
The attacks are also notable for employing a variety of custom tools for carrying out post-exploitation activities. This includes –
- Two C/C++-based binaries (wnet.exe and utility.exe) to enumerate all the resources on a network,
- A Python script (help.py) to establish an infinite communication loop with the C2 server and receive instructions to steal files with certain extensions, delete files created by other malware, and capture screenshots, and
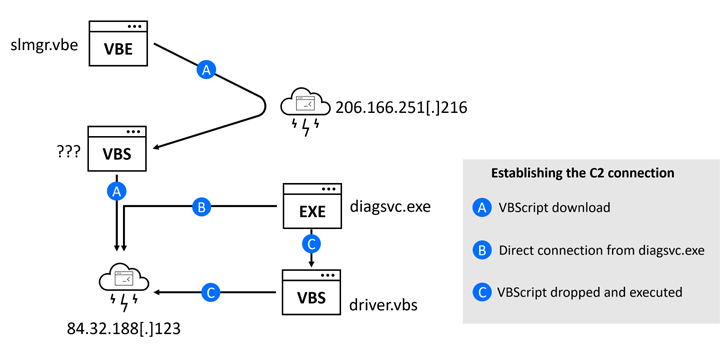
- A C++-based malware (diagsvc.exe aka DownEx) that’s chiefly designed to exfiltrate files to the C2 server
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
Two other variants of DownEx have also been earthed, the first of which executes an intermediate VBScript to harvest and transmit the files in the form of a ZIP archive.
The other version, which is downloaded via a VBE script (slmgr.vbe) from a remote server, eschews C++ for VBScript, but retains the same functionality as the former.
“This is a fileless attack – the DownEx script is executed in memory and never touches the disk,” Bitdefender said. “This attack highlights the sophistication of a modern cyberattack. Cybercriminals are finding new methods for making their attacks more reliable.”