The Android banking fraud malware known as SharkBot has reared its head once again on the official Google Play Store, posing as file managers to bypass the app marketplace’s restrictions.
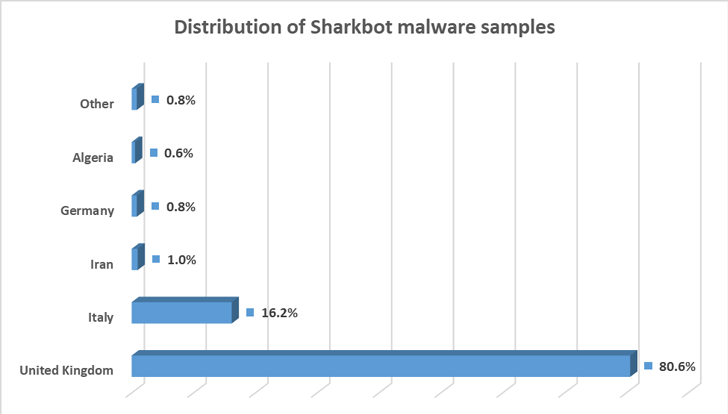
A majority of the users who downloaded the rogue apps are located in the U.K. and Italy, Romanian cybersecurity company Bitdefender said in an analysis published this week.
SharkBot, first discovered towards the end of 2021 by Cleafy, is a recurring mobile threat distributed both on the Google Play Store and other third-party app stores.
One of the trojan’s primary goals is to initiate money transfers from compromised devices via a technique called “Automatic Transfer System” (ATS), in which a transaction triggered via a banking app is intercepted to swap the payee account with an actor-controlled account in the background.
It’s capable of serving a fake login overlay when users attempt to open legitimate banking apps, stealing the credentials in the process.
Often, such apps offer seemingly harmless functionality, masquerading as antivirus software and cleaners to sneak into Google Play Store. But they also double up as droppers that, once installed on the device, can fetch the malware payload.
The dropper apps, now taken down, are below –
- X-File Manager (com.victorsoftice.llc) – 10,000+ downloads
- FileVoyager (com.potsepko9.FileManagerApp) – 5,000+ downloads
- LiteCleaner M (com.ltdevelopergroups.litecleaner.m) – 1,000+ downloads
LiteCleaner M is still available for download from a third-party app store called Apksos, which also houses a fourth SharkBot artifact by the name “Phone AID, Cleaner, Booster” (com.sidalistudio.developer.app).
The X-File Manager app, which is only accessible to users in Italy, attracted over 10,000 downloads before it was removed. With Google steadily clamping down on permission abuse, the threat actor’s choice of using a file manager as a lure is not surprising.
That’s because Google’s Developer Program Policy restricts the permission to install external packages (REQUEST_INSTALL_PACKAGES) to a handful of app categories: web browsers, instant messengers that support attachments, file managers, enterprise device management, backup and restore, and device transfer.
Invariably, this permission is abused to download and install malware from a remote server. Some of the targeted bank apps include Bank of Ireland, Bank of Scotland, Barclays, BNL, HSBC U.K., Lloyds Bank, Metro Bank, and Santander.
“The application [i.e., the dropper] performs anti-emulator checks and targets users from Great Britain and Italy by verifying if the SIM ISO corresponds with IT or GB,” Bitdefender researchers said.
Users who have installed the aforementioned apps are recommended to delete them and change their bank account passwords immediately. Users are also advised to enable Play Store Protect, and scrutinize app ratings and reviews before downloading them.