A cybercrime enterprise known as Lemon Group is leveraging millions of pre-infected Android smartphones worldwide to carry out their malicious operations, posing significant supply chain risks.
“The infection turns these devices into mobile proxies, tools for stealing and selling SMS messages, social media and online messaging accounts and monetization via advertisements and click fraud,” cybersecurity firm Trend Micro said.
The activity encompasses no fewer than 8.9 million compromised Android devices, particularly budget phones, with a majority of the infections discovered in the U.S., Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, the Philippines, and Argentina.
The findings were presented by researchers Fyodor Yarochkin, Zhengyu Dong, Vladimir Kropotov, and Paul Pajares at the Black Hat Asia conference held in Singapore last week.
Describing it as a continuously evolving problem, the cybersecurity firm said the threat actors are branching out to other Android-based IoT devices such as Smart TVs, Android TV boxes, entertainment systems, and even children’s watches.
The infections are globally spread across in over 180 countries, with over 50 brands of mobile devices compromised by a malware strain called Guerilla.
“Following our timeline estimates, the threat actor has spread this malware over the last five years,” the researchers said. “A compromise on any significant critical infrastructure with this infection can likely yield a significant profit for Lemon Group in the long run at the expense of legitimate users.”
Guerilla was first documented by Sophos in 2018 when it discovered 15 apps uploaded on the Play Store that harbored functionality to engage in click fraud and act as a backdoor.
The malware also attracted attention in early 2022 for its ability to intercept SMS messages that match predefined characteristics such as one-time passwords (OTPs) associated with various online platforms, shortly after which the threat actor changed the name of the undertaking from Lemon to Durian Cloud SMS.
The goal, per Trend Micro, is to bypass SMS-based verification and advertise bulk virtual phone numbers – which belong to unsuspecting users of the infected Android handsets – for sale to create online accounts.
While such services have a privacy benefit, allowing users to sign up for services using temporary or disposable phone numbers, they can also be abused to create spam accounts on a large scale and conduct fraud.
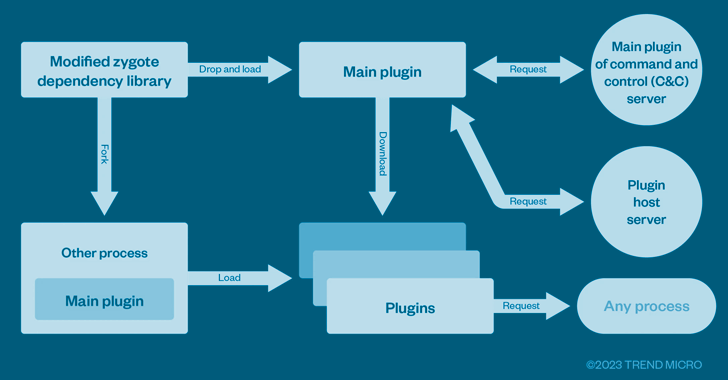
The latest findings from the cybersecurity company illustrate that the SMS grabbing feature is just one of the many plugins associated with a downloader component (aka the main plugin) that’s loaded into a zygote process by means of a tampered library.
It’s worth noting that the same technique of modifying the zygote process has also been adopted by another mobile trojan called Triada.
“With this, every time other app processes are forked from the zygote, it would also be tampered,” the researchers said. “The main plugin will load other plugins with the current process being the target, and the other plugins will try to control the current app via a hook.”
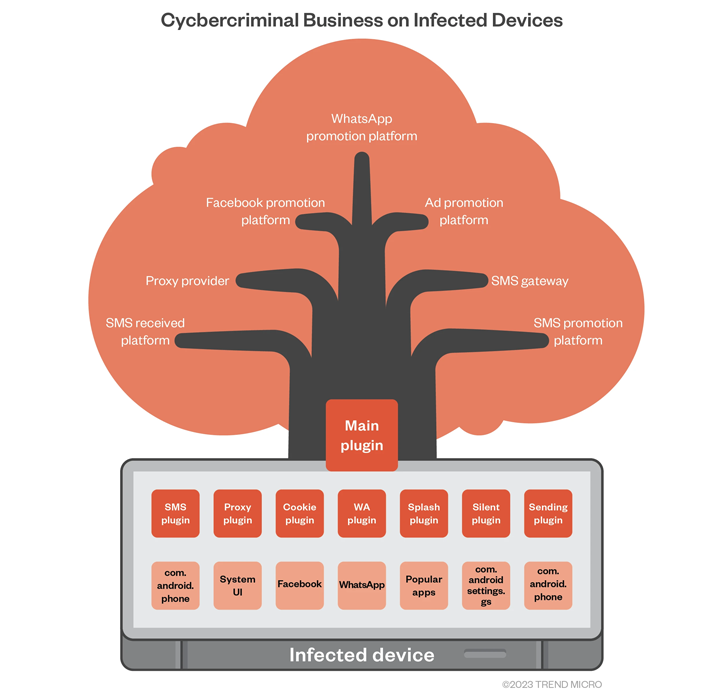
Each of the Guerilla plugins serves a particular business function and a monetization opportunity for the Lemon Group actors. Some of them are listed below –
- Proxy plugin to setup reverse proxy from an infected phone and allow other actors to rent out access to the network resources of the affected mobile device
- Cookie plugin to harvest users’ Facebook cookies and other profile information
- WhatsApp plugin to hijack sessions and send unwanted messages
- Splash plugin to serve unwarranted ads when launching certain apps, and
- Silent plugin to stealthily install an APK file and launch the app
Further investigation into the sprawling operation has unraveled infrastructure overlaps Lemon Group and Triada, suggesting that the two groups may have collaborated at some point.
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
Save My Seat!
The unauthorized firmware modifications are believed to have occurred via an unnamed third-party vendor that “produces the firmware components for mobile phones” and which also manufactures similar components for Android Auto.
The disclosure comes as Microsoft security researcher Dimitrios Valsamaras detailed a new attack method dubbed Dirty Stream that turns Android share targets into a vector for distributing malicious payloads and capturing sensitive data from other apps installed on a device.
“The concept is similar to a file upload vulnerability of a web application,” Valsamaras said. “More specifically, a malicious app uses a specially crafted content provider to bear a payload that it sends to the target application.”
“As the sender controls the content but also the name of the stream, the receiver may overwrite critical files with malicious content in case it doesn’t perform some necessary security checks. Additionally, when certain conditions apply, the receiver may also be forced to copy protected files to a public directory, setting the user’s private data at risk.”