A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines (VMs) to install third-party remote management tools within compromised environments.
Google-owned Mandiant attributed the activity to a threat group it tracks under the name UNC3944, which is also known as Roasted 0ktapus and Scattered Spider.
“This method of attack was unique in that it avoided many of the traditional detection methods employed within Azure and provided the attacker with full administrative access to the VM,” the threat intelligence firm said.
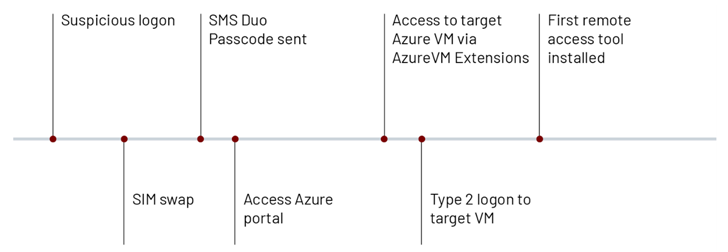
The emerging adversary, which first came to light in late last year, is known to leverage SIM swapping attacks to breach telecommunications and business process outsourcing (BPO) companies since at least May 2022.
Subsequently, Mandiant also found UNC3944 utilizing a loader named STONESTOP to install a malicious signed driver dubbed POORTRY that’s designed to terminate processes associated with security software and delete files as part of a BYOVD attack.
It’s currently not known how the threat actor conducts the SIM swaps, although the initial access methodology is suspected to involve the use of SMS phishing messages targeting privileged users to obtain their credentials and then staging a SIM swap to receive the two-factor authentication (2FA) token to a SIM card under their control.
Armed with the elevated access, the threat actor then moves to survey the target network by exploiting Azure VM extensions such as Azure Network Watcher, Azure Windows Guest Agent, VMSnapshot, and Azure Policy guest configuration.
Learn to Stop Ransomware with Real-Time Protection
Join our webinar and learn how to stop ransomware attacks in their tracks with real-time MFA and service account protection.
Save My Seat!
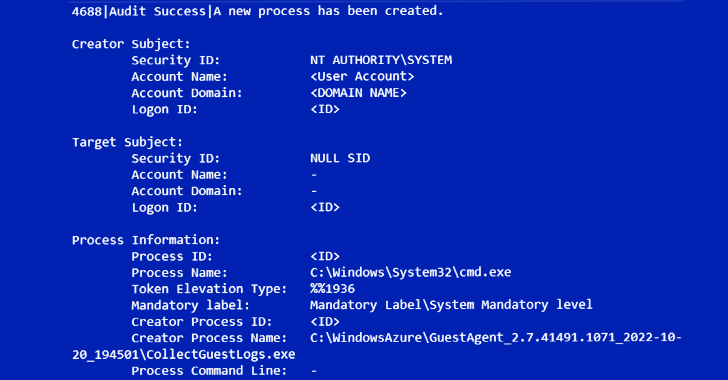
“Once the attacker completes their reconnaissance, they employ the serial console functionality in order to gain an administrative command prompt inside of an Azure VM,” Mandiant said, adding it observed UNC3944 making use of PowerShell to deploy legitimate remote administration tools.
The development is yet another evidence of attackers taking advantage of living-off-the-land (LotL) techniques to sustain and advance an attack, while simultaneously circumventing detection.
“The novel use of the serial console by attackers is a reminder that these attacks are no longer limited to the operating system layer,” Mandiant said.
“Unfortunately, cloud resources are often poorly misunderstood, leading to misconfigurations that can leave these assets vulnerable to attackers. While methods of initial access, lateral movement, and persistence vary from one attacker to another, one thing is clear: Attackers have their eyes on the cloud.”